Grok#
The grok module allows you to extract data from complicated text structures without specifying the whole regular expression every time. Instead, grok assigns names to regular expressions, allowing the user to specify the name instead. Grok patterns may contain additional patterns nested within them, making it easy to build up new definitions. It pre-defines a selection of useful patterns, but can also read your own customized set of patterns from a resource.
By default, grok passes through any entry which matches the pattern and drops any which does not. This behavior can be inverted with the -v flag.
Grok is a filtering module; after specifying the desired pattern, you may also specify a list of filters to apply to the extracted fields.
Note
Because some filters incorporate extremely strict and complex patterns, they can be relatively slow when processing large numbers of entries. Use modules such as grep, regex, and words to pre-filter as much as possible.
Supported Options#
-e <arg>: Operate on the specified enumerated value instead of the entire record.-r <resource>: load custom grok patterns from the resource with the specified name, rather than the defaultgrokresource.-v: Operate in inverse mode; entries which do not match the pattern will be passed, and entries which do match will be dropped. You cannot specify any filters when using this flag.-p: The “-p” option tells grok to allow entries through if the expression does not match at all. The permissive flag does not change the operation of filters.
Parse Apache Logs#
The following query takes advantage of a resource to implement a complex pattern to strictly process Apache2.0 combined access logs. The COMBINEDAPACHELOG pattern is part of the very large pattern set provided by Gravwell on github. Download the pattern set and upload it as a resource name grok to gain access to a massive suite of predefined grok patterns.
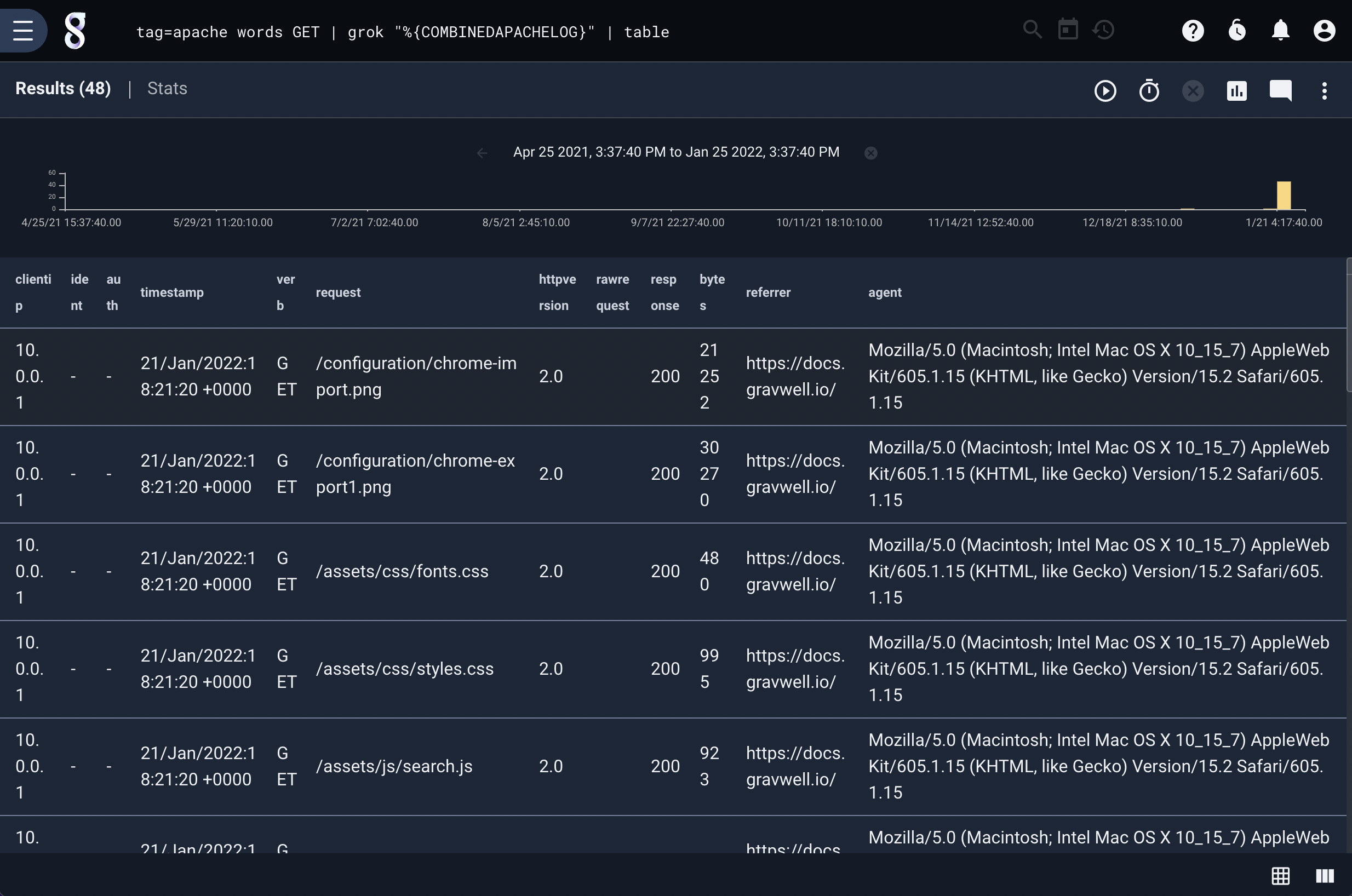
The following query finds all Apache logs for “GET” requests and parses them out into their components:
tag=apache words GET | grok "%{COMBINEDAPACHELOG}" | table
Note
This query may take some time if you have millions of entries since the COMBINEDAPACHELOG pattern is complex and very strict.
Filtering#
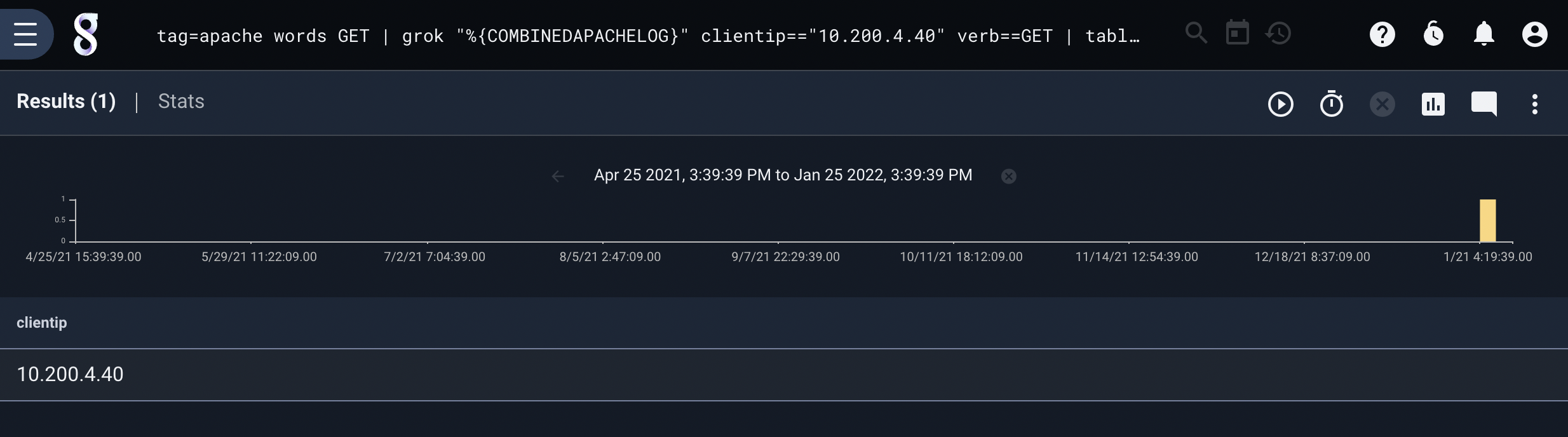
We can build on the previous query to return only those entries whose “clientip” field matches a particular IP and uses the GET method:
tag=apache words GET | grok "%{COMBINEDAPACHELOG}" clientip=="10.200.4.40" verb==GET | table clientip
Note
We filter for PUT and the IP using the words module to engage indexing and reduce the number of entries that are processed by the expensive COMBINEDAPACHELOG grok pattern.
Performance#
Grok can dramatically simplify complicated regular expressions and allow mere mortals to crack apart large log fragments. However, a grok pattern designed to extract and validate every field in a log is going to be complex and slow. If you don’t need every field, consider using fragments and primitives. A smaller grok pattern that only extracts a few items can be dramatically faster than a complete pattern that extracts everything.
For example, let’s look at two queries that compile response code counts for each HTTP method and display them in a stackgraph. The first query uses grok with the COMBINEDAPACHELOG pattern for a very simple query:
tag=apache grok "%{COMBINEDAPACHELOG}" | stats count by verb response | stackgraph verb response count
The second query uses grok primitives to extract only the fields that are explicitly needed:
tag=apache grok "] \"%{WORD:verb}\s\S+\s\S+\s%{POSINT:response}" | stats count by verb response | stackgraph verb response count
Both queries produce identical results:
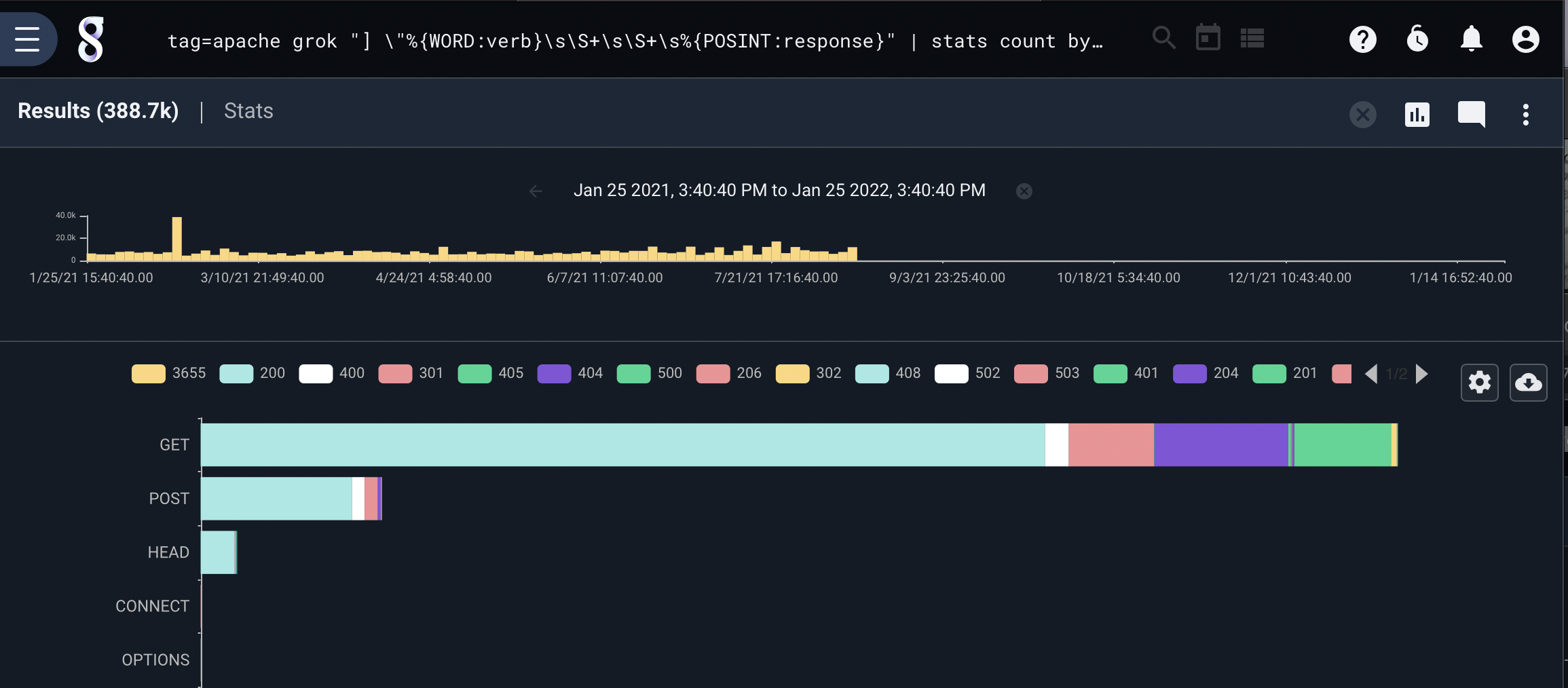
However, to process 10M Apache access logs the first query took 2m 39s. The second query took only 3.46s, that is over a 45X speedup. So while the simpler query looks great, it can be worth your time to work with primitive patterns when working on large data sets.
Pre-defined Patterns#
The Grok module provides a base set of predefined patterns that are ready for use. These base patterns cover basic data types and are generally very strict about what they will and will not accept, for a large set of patterns designed to handle entire log sets see our the published resource on github
Pattern Name |
Substitution Pattern |
|---|---|
USERNAME |
|
USER |
|
EMAILLOCALPART |
|
HOSTNAME |
|
EMAILADDRESS |
|
HTTPDUSER |
|
INT |
|
BASE10NUM |
|
NUMBER |
|
BASE16NUM |
|
BASE16FLOAT |
|
POSINT |
|
NONNEGINT |
|
WORD |
|
NOTSPACE |
|
SPACE |
|
DATA |
|
GREEDYDATA |
|
QUOTEDSTRING |
``(“(.|[^"]+)+”)|””|(‘(.|[^']+)+’)|’’|(`(. |
UUID |
|
UNIXPATH |
|
TTY |
|
WINPATH |
|
PATH |
|
URIPROTO |
|
URIHOST |
|
URIPATH |
|
URIPARAM |
|
URIPATHPARAM |
|
URI |
|
MONTH |
|
MONTHNUM |
|
MONTHNUM2 |
|
MONTHDAY |
|
DAY |
|
YEAR |
|
HOUR |
|
MINUTE |
|
SECOND |
|
TIME |
|
DATE_US |
|
DATE_EU |
|
DATE_X |
|
ISO8601_TIMEZONE |
|
ISO8601_SECOND |
|
TIMESTAMP_ISO8601 |
|
DATE |
|
DATESTAMP |
|
TZ |
|
NUMTZ |
|
DATESTAMP_RFC822 |
|
DATESTAMP_RFC2822 |
|
DATESTAMP_OTHER |
|
DATESTAMP_EVENTLOG |
|
HTTPDERROR_DATE |
|
ANSIC |
|
UNIXDATE |
|
RUBYDATE |
|
RFC822Z |
|
RFC850 |
|
RFC1123 |
|
RFC1123Z |
|
RFC3339 |
|
RFC3339NANO |
|
KITCHEN |
|
SYSLOGTIMESTAMP |
|
LOGLEVEL |
|
QS |
|
NQS |
|
PROG |
|
CISCOMAC |
|
WINDOWSMAC |
|
COMMONMAC |
|
MAC |
|
IPV4 |
|
IPV6 |
|
IP |
|
IPORHOST |
|
HOSTPORT |
|
HTTPDATE |
|