Windows Event Service#
The Gravwell Windows events ingester runs as a service on a Windows machine and sends Windows events to the Gravwell indexer. The ingester consumes from the System, Application, Setup, and Security channels in the default configuration. Each channel can be configured to consume from a specific set of events or providers.
Basic Configuration#
The Windows Event ingester uses the unified global configuration block described in the ingester section. Like most other Gravwell ingesters, the Windows Event ingester supports multiple upstream indexers, TLS, cleartext, and named pipe connections, a local cache, and local logging.
Global Options#
In addition to the unified global configuration block described in the ingester section, the Windows Event ingester has a few additional global configuration options:
Bookmark-Location: The ingester uses a ‘bookmark’ file to keep track of where it is in event channels between runs. This file is normally placed in the ingester’s Program Data directory in a file named “bookmark”, but this parameter may be used to override that location.Ignore-Timestamps: If set, the ingester will ignore any timestamps on the events it reads and instead apply the current time. This is rarely desirable!
EventChannel configuration#
An EventChannel maps Windows event channels to Gravwell tags and specifies any additional options desired.
Channel: The channel to read Windows events from, e.g. “System”.Tag-Name: The tag to which events should be sent.Max-Reachback: By default, when an EventChannel starts for the first time, it will ingest whatever events are available on the channel – which may be a significant amount of data! SettingMax-Reachback=24hinstead tells the EventChannel to ignore any events older than 24 hours on first run. After the first run, the ingester will ‘bookmark’ the last event it saw and only read entries from that point on.Level: Specifies the severity level of entries which should be read: verbose, information, warning, error, critical. May be specified multiple times to read multiple levels. Default is to read all levels.Provider: Specifies that the EventChannel should only read logs from a given provider, e.g. “Windows System”. May be specified multiple times.EventID: Specifies that the EventChannel should only read logs with a particular numeric event ID. May be specified multiple times.Request-Size: Number of events to request at a time, default 128, max 1024. A higher value can give higher throughput.Request-Buffer: Sets a size in megabytes to read at a time, default 2, maximum 32. A higher value can give higher throughput.
Note
Once Max-Reachback has been defined for an EventChannel and the ingester has been started, it is not trivially possible to change your mind and reset the Max-Reachback to an older time. Your best option is to change the name of the EventChannel (e.g. [EventChannel "system"] becomes [EventChannel "system-fixed"]) and restart the ingester, but be aware that this will cause some events to be ingested twice.
EventChannel Examples#
[EventChannel "system"]
Tag-Name=windows
Channel=System #pull from the system channel
[EventChannel "sysmon"]
Tag-Name=sysmon
Channel="Microsoft-Windows-Sysmon/Operational"
Max-Reachback=24h #reachback must be expressed in hours (h), minutes (m), or seconds(s)
[EventChannel "Application"]
Channel=Application #pull from the application channel
Tag-Name=winApp #Apply a new tag name
Provider=Windows System #Only look for the provider "Windows System"
EventID=1000-4000 #Only look for event IDs 1000 through 4000
EventID=1,2,3,4 #also look for events 1, 2, 3, and 4
Level=verbose #Only look for verbose entries
Max-Reachback=72h #start looking for logs up to 72 hours in the past
Request-Buffer=16 #use a large 16MB buffer for high throughput
Request-Size=1024 #Request up to 1024 entries per API call for high throughput
[EventChannel "System Critical and Error"]
Channel=System #pull from the system channel
Tag-Name=winSysCrit #Apply a new tag name
Level=critical #look for critical entries
Level=error #AND for error entries
Max-Reachback=96h #start looking for logs up to 96 hours in the past
[EventChannel "Security prune"]
Channel=Security #pull from the security channel
Tag-Name=winSec #Apply a new tag name
EventID=-400 #ignore event ID 400
EventID=-401 #AND ignore event ID 401
Installation#
Download the Gravwell Windows Events installer:
Ingester Name |
Installer |
More Info |
|---|---|---|
Windows Events |
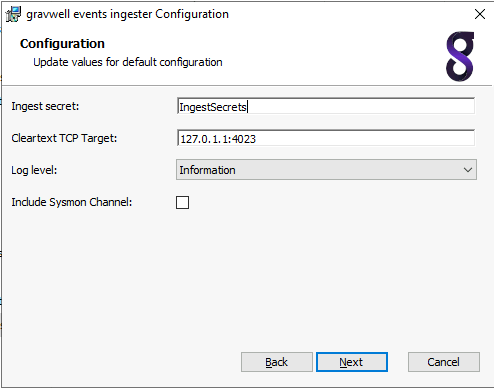
Run the .msi installation wizard to install the Gravwell events service. On first installation the installation wizard will prompt to configure the indexer endpoint and ingest secret. Subsequent installations and/or upgrades will identify a resident configuration file and will not prompt.
Note
The Log Level selection is for internal logging only, it does not affect which Windows events are captured by the ingester. Setting the level to Information will cause the ingester to emit log events when it starts, stops, and attaches to event Channels.
The ingester is configured with the config.cfg file located at %PROGRAMDATA%\gravwell\eventlog\config.cfg. The configuration file follows the same form as other Gravwell ingesters with a [Global] section configuring the indexer connections and multiple EventChannel definitions.
To modify the indexer connection or specify multiple indexers, change the connection IP address to the IP of your Gravwell server and set the Ingest-Secret value. This example shows configuring an encrypted transport:
Ingest-Secret=YourSecretGoesHere
Encrypted-Backend-target=ip.addr.goes.here:port
Once configured, this file can be copied to any other Windows system from which you would like to collect events.
Silent Installation#
The Windows event ingester is designed to be compatible with an automated deployment. This means that a domain controller can push the installer to clients and invoke installation without user interaction. To force a silent installation execute the installer with administrative privileges via msiexec with the /quiet argument. This installation method will install the default configuration and start the service.
To configure your specific parameters you will then need to either push a modified configuration file to %PROGRAMDATA%\gravwell\eventlog\config.cfg and restart the service, or also provide the CONFIGFILE argument with the fully qualified path to the config.cfg file.
Note that you may need to create the %PROGRAMDATA%\gravwell\eventlog path.
A complete execution sequence for a Group Policy push might look like:
msiexec.exe /i gravwell_win_events_5.1.4.msi /quiet
xcopy \\share\gravwell_config.cfg %PROGRAMDATA%\gravwell\eventlog\config.cfg
sc stop "GravwellEvents Service"
sc start "GravwellEvents Service"
Or
msiexec.exe /i gravwell_win_events_3.3.12.msi /quiet CONFIGFILE=\\share\gravwell_config.cfg
Troubleshooting#
You can verify the Windows ingester connectivity by navigating to the Ingester page on the web interface. If the Windows ingester is not present, check the status of the service either via the windows GUI or by running sc query GravwellEvents at the command line.
If the ingester has successfully connected you can navigate to the Ingesters & Federators page and look for the ingester in the list. It will be labeled under the “winevent” section.
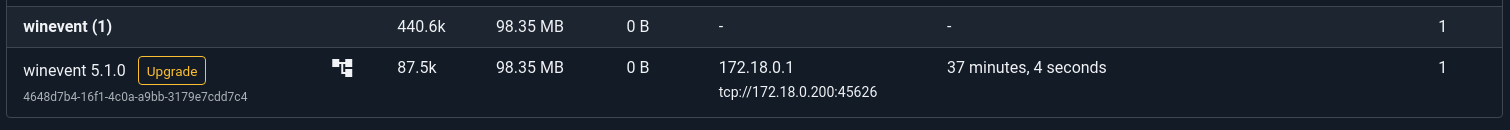
Clicking on the listed ingester will show the functional configuration as well as some additional data about the Event channels being monitored.

Optional Sysmon Integration#
The Sysmon utility, part of the sysinternals suite, is an effective and popular tool for monitoring Windows systems. There are plenty of resources with examples of good sysmon configuration files. At Gravwell, we like to use the modular sysmon config on github from olafhartong.
Edit the Gravwell Windows agent config file located at %PROGRAMDATA%\gravwell\eventlog\config.cfg and add the following lines:
[EventChannel "Sysmon"]
Tag-Name=sysmon #Apply a new tag name
Provider=Microsoft-Windows-Sysmon #Only look for the provider
Channel=Microsoft-Windows-Sysmon/Operational
Download the default sysmon configuration file
Install sysmon with your configuration using an administrator shell (Powershell works too) by running the following command:
sysmon.exe -accepteula -i sysmonconfig-export.xml
Restart the Gravwell service via standard windows service management.
Example Configuration with Sysmon#
[EventChannel "system"]
Tag-Name=windows
#no Provider means accept from all providers
#no EventID means accept all event ids
#no Level means pull all levels
#no Max-Reachback means look for logs starting from now
Channel=System #pull from the system channel
[EventChannel "application"]
Tag-Name=windows
Channel=Application #pull from the system channel
[EventChannel "security"]
Tag-Name=windows
Channel=Security #pull from the system channel
[EventChannel "setup"]
Tag-Name=windows
Channel=Setup #pull from the system channel
[EventChannel "sysmon"]
Tag-Name=windows
Provider=Microsoft-Windows-Sysmon #Only look for the provider
Channel=Microsoft-Windows-Sysmon/Operational
Windows Event Forwarding#
The Gravwell Winevent ingester can be combined with Windows Event Forwarding (WEF) to simplify deployments and reduce the number of endpoints the ingester must be installed on. Windows Event Forwarding is an integrated Windows service that forwards events to a central collection point using integrated Windows functionality. More information on WEF can be found on several Microsoft resources.
Configuring Windows Event Forwarding is beyond the scope of this document, but actually collecting the forwarded events is very simple.
First you will need to install the winevent ingester on the Windows system that will be receiving the forwarded events. Then you will want to validate the name of the channel that is configured to receive the forwarded events on the collection box. Typically that is ForwardedEvents.
Note
Forwarded events will still contain the correct Channel in their logs.
To enable the collection of forwarded events first we need to open the winevent configuration file located at %PROGRAMDATA%\gravwell\eventlog\config.cfg as an Administrator and insert a new Listener stanza that is pointed at the WEF collection channel:
[EventChannel "WEF Events"]
Tag-Name=windows
Channel=ForwardedEvents
Example Windows Searches#
Assuming the default tag names are used, to see ALL sysmon entries in their entirety run this search:
tag=sysmon
To see ALL Windows events in their entirety run:
tag=windows
For the following searches we can use the winlog search module to filter and extract specific events and fields. To see all network connection rates per computer using sysmon data:
tag=sysmon winlog Provider == "Microsoft-Windows-Sysmon" EventID == 3 Protocol |
stats count by Protocol |
chart count by Protocol
To show all successful logons across all logon types (including service logons) using standard Windows logs:
tag=windows words User32 4624
| winlog Provider=="Microsoft-Windows-Security-Auditing" EventID==4624 LogonType LogonProcessName=="User32 "
TargetUserName Computer TargetDomainName
| lookup -r windows_login_types LogonType logon_type name as LogonType
| table TargetUserName Computer TargetDomainName LogonType TIMESTAMP
Note
The above query needs to have the windows_login_types resource that is provided by the Windows Resource kit.